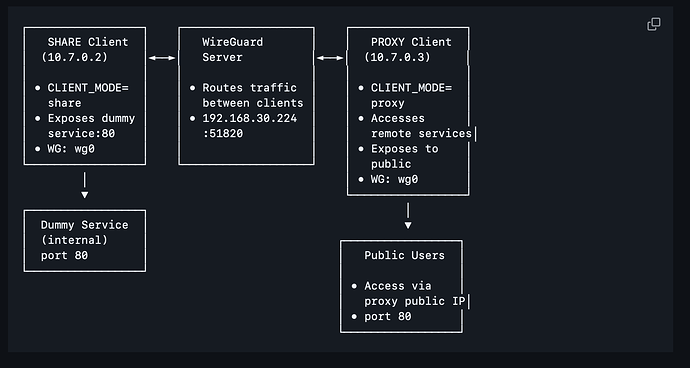
Da ich es einfach wissen wollte, habe ich folgendes Projekt erstellt: wg-service-proxy
Wie man am Screenshot sieht wird auf einer Seite Nginx Dummy Container mit Port 80 in den Tunnel eingebunden (Sharing) und somit für die weiteren Clients im Wireguard Netz erreichbar gemacht.
Ein Proxy Client könnte dann das Service auf einen anderen Host wieder zugänglich machen und zum Beispiel über einen Ingress Proxy (traefix, nginx, …) zugänglich machen.
Sharing Container:
docker exec -it wireguard-go-app sh
/app # iptables -vnL
Chain INPUT (policy ACCEPT 114 packets, 12960 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- wg0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
0 0 ACCEPT udp -- wg0 * 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
0 0 ACCEPT udp -- wg0 * 0.0.0.0/0 0.0.0.0/0 udp dpt:51820
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- wg0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * wg0 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 172.27.0.2 tcp dpt:80
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 172.27.0.2 tcp dpt:80
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
/app # iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.27.0.2:80
0 0 DNAT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:172.27.0.2:80
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1 packets, 176 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER_OUTPUT all -- * * 0.0.0.0/0 127.0.0.11
Chain POSTROUTING (policy ACCEPT 1 packets, 176 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER_POSTROUTING all -- * * 0.0.0.0/0 127.0.0.11
0 0 MASQUERADE all -- * wg0 0.0.0.0/0 0.0.0.0/0
0 0 MASQUERADE tcp -- * * 0.0.0.0/0 172.27.0.2 tcp dpt:80
0 0 MASQUERADE tcp -- * * 0.0.0.0/0 172.27.0.2 tcp dpt:80
Chain DOCKER_OUTPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- * * 0.0.0.0/0 127.0.0.11 tcp dpt:53 to:127.0.0.11:43225
0 0 DNAT udp -- * * 0.0.0.0/0 127.0.0.11 udp dpt:53 to:127.0.0.11:33365
Chain DOCKER_POSTROUTING (1 references)
pkts bytes target prot opt in out source destination
0 0 SNAT tcp -- * * 127.0.0.11 0.0.0.0/0 tcp spt:43225 to::53
0 0 SNAT udp -- * * 127.0.0.11 0.0.0.0/0 udp spt:33365 to::53
/app # ip route show
default via 172.26.0.1 dev eth0
default dev wg0 scope link metric 1000
10.7.0.0/24 dev wg0 scope link
172.26.0.0/16 dev eth0 proto kernel scope link src 172.26.0.2
172.27.0.0/16 dev eth1 proto kernel scope link src 172.27.0.3
/app #
Proxy Container:
docker exec -it wireguard-go-app sh
/app # iptables -vnL
Chain INPUT (policy ACCEPT 282 packets, 44646 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT icmp -- wg0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
0 0 ACCEPT tcp -- wg0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
0 0 ACCEPT udp -- wg0 * 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
0 0 ACCEPT udp -- wg0 * 0.0.0.0/0 0.0.0.0/0 udp dpt:51820
0 0 LOG tcp -- eth0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 LOG flags 0 level 4 prefix "WG-PUBLIC: "
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
10 2242 ACCEPT all -- wg0 * 0.0.0.0/0 0.0.0.0/0
14 890 ACCEPT all -- * wg0 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT tcp -- eth0 wg0 0.0.0.0/0 10.7.0.2 tcp dpt:80
0 0 ACCEPT tcp -- wg0 eth0 10.7.0.2 0.0.0.0/0 tcp spt:80
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
/app # iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 126 packets, 48001 bytes)
pkts bytes target prot opt in out source destination
2 120 DNAT tcp -- eth0 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 to:10.7.0.2:80
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 1 packets, 176 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER_OUTPUT all -- * * 0.0.0.0/0 127.0.0.11
Chain POSTROUTING (policy ACCEPT 1 packets, 176 bytes)
pkts bytes target prot opt in out source destination
0 0 DOCKER_POSTROUTING all -- * * 0.0.0.0/0 127.0.0.11
2 120 MASQUERADE all -- * wg0 0.0.0.0/0 0.0.0.0/0
0 0 MASQUERADE tcp -- * eth0 0.0.0.0/0 10.7.0.2 tcp dpt:80
Chain DOCKER_OUTPUT (1 references)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- * * 0.0.0.0/0 127.0.0.11 tcp dpt:53 to:127.0.0.11:40219
0 0 DNAT udp -- * * 0.0.0.0/0 127.0.0.11 udp dpt:53 to:127.0.0.11:34763
Chain DOCKER_POSTROUTING (1 references)
pkts bytes target prot opt in out source destination
0 0 SNAT tcp -- * * 127.0.0.11 0.0.0.0/0 tcp spt:40219 to::53
0 0 SNAT udp -- * * 127.0.0.11 0.0.0.0/0 udp spt:34763 to::53
/app # ip route show
default via 172.19.0.1 dev eth0
10.7.0.0/24 dev wg0 scope link
172.18.0.0/16 dev eth1 proto kernel scope link src 172.18.0.2
172.19.0.0/16 dev eth0 proto kernel scope link src 172.19.0.2
/app #
WG Server:
root@nfndeb13-dev:~# wg
interface: wg0
public key: xv0p7FLk/NVeTBSTj9j3qk8bgunpfyn0weLKi/y8iUM=
private key: (hidden)
listening port: 51820
peer: fvc7/8VvpLGDUFK3XbqA9xnxwmPSVI1188SAD91vO0g=
preshared key: (hidden)
endpoint: 192.168.30.14:45344
allowed ips: 10.7.0.2/32
latest handshake: 26 seconds ago
transfer: 80.38 KiB received, 27.12 KiB sent
peer: yeGLQ4sI+RCiwkTzGGPad7QbjRYjT8h0bqQ/H5eC8UA=
preshared key: (hidden)
endpoint: 192.168.30.5:41444
allowed ips: 10.7.0.3/32
latest handshake: 1 minute, 50 seconds ago
transfer: 45.33 KiB received, 16.20 KiB sent
Test Proxy Seite: curl http://localhost
Welcome to nginx! html { color-scheme: light dark; } body { width: 35em; margin: 0 auto; font-family: Tahoma, Verdana, Arial, sans-serif; }Welcome to nginx!
If you see this page, the nginx web server is successfully installed and working. Further configuration is required.
For online documentation and support please refer to
nginx.org.
Commercial support is available at
nginx.com.
Thank you for using nginx.
Test WG-Server: curl http://10.7.0.2
Welcome to nginx! html { color-scheme: light dark; } body { width: 35em; margin: 0 auto; font-family: Tahoma, Verdana, Arial, sans-serif; }Welcome to nginx!
If you see this page, the nginx web server is successfully installed and working. Further configuration is required.
For online documentation and support please refer to
nginx.org.
Commercial support is available at
nginx.com.
Thank you for using nginx.
Einfach einmal testen. ![]()
Und ja es gibt da noch Pangolin / Gerbil … aber so macht es mehr Spass …